Remk Ransomware Removal Guide
Do you know what happens when Remk Ransomware slithers into your Windows operating system? This infection encrypts files, and it encrypts the most precious ones, including photos, videos, or documents. There are tons of different types of files that are identified as personal, and this malware can go after all of them. The infection does not leave one stone unturned. Unfortunately, once the attack is complete, you might find all of your personal files corrupted. Since you are reading this report, it is likely that you have already faced this dangerous infection. If that has happened, you should not panic because that is exactly what the attackers behind the infection want. If you are panicked, they can manipulate you more easily, and you must not give in. The good news is that there is a possibility that you could restore all files after deleting Remk Ransomware. If you would like to learn more about the removal of this pest, please continue reading.
To understand Remk Ransomware better, we need to understand how it spreads. According to our malware researchers, this malicious infection is most likely to use spam emails, malicious downloaders, and unpatched vulnerabilities within your system. Needless to say, your system cannot be infected with malware just because someone sends you a misleading email. You have to be tricked into clicking an attached file or link first, which means that some of your involvement is needed too. Obviously, you have to be careful. Even if you are able to evade Remk Ransomware, there are tons of other infections that could try to slither in. This ransomware itself has clones that are part of the STOP Ransomware family. A few of them include Lokd Ransomware, Rezm Ransomware, and Topi Ransomware. The names of these infections usually come from the extensions that they add to the corrupted files. The Remk infection adds “.remk” to the corrupted files. Do not waste your time removing this extension or renaming files. That will not help.
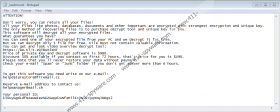
When Remk Ransomware encrypts files, it also drops a text file to the %HOMEDRIVE% directory. This file is named “_readme.txt,” and you can open it without causing more harm to your files. The purpose of the message is to introduce you to the attackers’ contact email addresses (helpdatarestore@firemail.cc and helpmanager@mail.ch) and inform you that a ransom payment is expected from you. Do you have 490 USD to spare? If you do not, you will not be able to pay the ransom for the decryptor that Remk Ransomware allegedly can provide you with. Well, even if you have the money, paying the ransom is the wrong move. The attackers can convince you to pay the ransom in return for a decryptor, but who’s to say that you would get it? Our experience indicates that you would not get a decryptor. The good news is that you do not need it. A tool named ‘STOP Decryptor’ was created by malware researchers, and you might be able to restore your files using it. Alternatively, you might have backup copies of the corrupted files, and if that is the case, you should be able to replace them.
According to our research team, Remk Ransomware installs itself to one specific location, and it only has one other file connected to it, which is the ransom note file in %HOMEDRIVE%. Due to this, the manual removal of this infection should be possible. If you want to delete the infection manually, you might be able to succeed with the guide below. We recommend that you remove Remk Ransomware using an anti-malware tool that was created to erase threats automatically. Besides taking care of that, the tool can also protect your operating system, which is just as important as getting rid of active threats. After you delete the infection and reconfigure Windows protection, you can try restoring files with the free decryptor or replacing them with copies that you own. Hopefully, you can restore all files and you do not need to face ransomware ever again.
How to delete Remk Ransomware
- Delete recently downloaded malware files (only if you can identify them).
- Tap Win+E keys at the same time to launch File Explorer.
- Enter %LOCALAPPDATA% into the field at the top.
- Delete a folder with a random name that contains malware files.
- Enter %HOMEDRIVE% into the field at the top.
- Delete the ransom note file named _readme.txt and also a folder named SystemID.
- Exit File Explorer and then Empty Recycle Bin.
- Perform a full system scan to check for malicious leftovers.
Remk Ransomware Screenshots: