Repl Ransomware Removal Guide
Researchers do not doubt that Repl Ransomware was based on threats belonging to the Stop Ransomware family. That is because the malicious application has a very similar working manner. Plus, it shows a note that is almost identical to messages shown by other threats belonging to the Stop Ransomware family. If you want to find out how this threat works and what its ransom note says, we encourage you to read our full report. We can also offer you our deletion instructions located below the text that show how you could delete Repl Ransomware manually. The process might be a bit complicated, and if you do not think you can handle it, we advise getting a reliable antimalware tool that could eliminate the ransomware.
Let us start with the malware’s distribution. Threats like Repl Ransomware can be spread through various channels. For example, the malicious application’s launchers could be sent to victims via email. In such a case, hackers could disguise malicious launcher to make it seem harmless. For example, they could make it look like a text document or a picture. Consequently, we highly recommend staying away from email attachments when they do not look suspicious or dangerous but come from unknown senders. If you have any doubts, you can always employ a reliable security tool that could scan the file in question and tell you whether it is malicious or not. Specialists advise doing the same with other files downloaded from the Internet as disguised malicious launchers can also be spread through various file-sharing websites, pop-ups, and ads. Therefore, we advise you never to let your guard down.
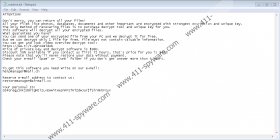
In case that Repl Ransomware is launched, the malware may create files mentioned in our deletion instructions. Such data might be needed to settle in and ensure that the malicious application can restart with the operating system. Afterward, the malware ought to begin the encryption process, during which it might encrypt all pictures, documents, and other personal files with a robust encryption algorithm. Each file that gets encrypted should be marked with the .repl extension, for example, penguin.jpg.repl. What happens next? The malicious application should create a ransom note called _readme.txt so that the victim would learn about what the threat did to his files. The ransom note should also contain instructions telling what to do to get special decryption tools that could decipher all encrypted files. In short, the note ought to say that users can purchase them or, in other words, pay a ransom. The note could also advise users to hurry up as it might say that those who contact Repl Ransomware’s creators in 72 hours receive a 50 percent discount.
However, it might not all go according to the plan explained on the malware’s ransom note. The truth is that hackers cannot provide any guarantees that you will receive the needed decryption tools. The only thing that they can prove is that they have decryption tools. Thus, we advise not to pay the ransom if you do not want to risk your savings for something that you might never get. Also, we recommend erasing Repl Ransomware because it could be dangerous to leave it on the system. If you want to learn how you could remove it manually, we advise checking the instructions below. The other way to eliminate Repl Ransomware is to scan your system with a reliable antimalware tool. Once the scan is over, you ought to be able to get rid of the identified ransomware and other items by pressing the given removal button.
Get rid of Repl Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Search for files named _readme.txt, right-click them, and select Delete.
- Check these locations:
%LOCALAPPDATA%
%USERPROFILE%\Local Settings\Application Data - Find the malware’s created folders with random names, e.g., 0215171b-ba55-7xal-a49s-c2fk4162159c, right-click them, and choose Delete.
- Navigate to this location: %WINDIR%\System32\Tasks
- Find a task titled Time Trigger Task, right-click it, and select Delete.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., SysHelper, right-click this value name, and press Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
Repl Ransomware Screenshots: