Revon Ransomware Removal Guide
Revon Ransomware is like Phobos Ransomware which is based on Chrysis/Dharma Ransomware. Thus, while it is a new threat, it works same as other malicious applications from the mentioned Chrysis/Dharma Ransomware family. If you have not encountered anything like this before, we encourage you to read our full report and learn more about this ransomware application. Also, at the end of this article, you can find our deletion instructions that show how to remove Revon Ransomware manually. Keep in mind that the process could be challenging and if it is too difficult for you, we recommend employing a reliable antimalware tool that could erase this malware. If you need more help with its deletion or have any questions about its working manner, feel free to leave us a message in the comments section.
Like most malicious applications from the Chrysis/Dharma Ransomware family Revon Ransomware could travel with malicious emails, installers, and via unsecured RDP (Remote Desktop Protocol) connections. Thus, the only way to avoid such threats is to never let your guard down. Meaning, you should never open files received via email if you are not one hundred percent sure that they are harmless or download installers that come from unreliable websites and are likely to be malicious. If you know that it is risky to interact with doubtful content, but still want to do it anyway, we advise at least scanning such data with a reliable antimalware tool first. Naturally, to stop malware from entering your system through unsecured RDP connections, you should ensure that they are well protected or disabled if you do not use them.
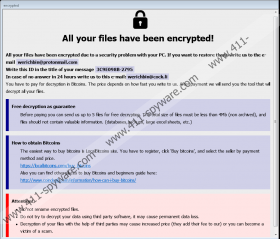
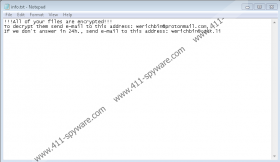
After Revon Ransomware’s installer is launched, the malicious application should create files that are mentioned in our deletion instructions, which you can find at the end of this article. Next, the malicious application should start encrypting files that could be valuable to you, for example, your photos, various documents, archives, and so on. If a file gets encrypted it should be marked with a second extension that has a unique ID number, which the threat generates for each infected computer. For instance, files that got encrypted on our test computer were marked with the following extension: .id[3C9E098B-2795].[werichbin@protonmail.com].revon. Next, the malware should drop a text file called info.txt that ought to contain a short ransom note. The longer ransom note’s version should be on the Revon Ransomware’s window that appears on top on the infected devices’ screens.
Like most ransom notes, the malware’s message says that files can only be decrypted with special decryption tools and that users must pay ransom to get them. Also, hackers may suggest sending a file for free decryption so that they could prove that they have the promised decryption tools. Lastly, to rush victims, the Revon Ransomware’s developers may say that the price will depend on how fast they contact them to get further instructions. We do not recommend rushing into anything or trusting hackers as there are no guarantees that they will hold on to their promises. If they do not, your money could be lost in vain and your files would still be encrypted. If you decide that it is enough that you lost your files, we advise concentrating on the malware’s deletion.
You could try to erase Revon Ransomware manually with the deletion instructions located below this paragraph. However, the task could be too challenging, which is why it might be easier and safer to use a reliable antimalware tool that could eliminate Revon Ransomware for you. Once the system is clean, it should be safe to replace encrypted files with backup copies if you have them.
Get rid of Revon Ransomware
- Click Ctrl+Alt+Delete.
- Pick Task Manager and go to the Processes tab.
- Check if there is a process belonging to the ransomware.
- Select it and press the End Task button.
- Close Task Manager.
- Press Win+E.
- Navigate to these directories:
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads
%TEMP% - Find the ransomware’s installer (suspicious recently downloaded file), right-click it, and select Delete.
- Go to these locations:
%LOCALAPPDATA%
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Find suspicious executable files that could belong to the ransomware, right-click them, and press Delete.
- Navigate to these locations:
%USERPROFILE%\Desktop
%HOMEDRIVE% - Search for files called Info.hta, right-click them and press Delete.
- Look for files called info.txt, right-click them, and press Delete.
- Close File Explorer.
- Press Win+R.
- Type Regedit and click Enter.
- Go to these locations:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Find value names belonging to the malware, right-click them, and press Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart your computer.
Revon Ransomware Screenshots: