Rezm Ransomware Removal Guide
Your actions matter, and if you are careless when you are using your computer, Rezm Ransomware could slither in without warning. This threat usually relies on spam emails and download bundles to slither in, but the launcher file is disguised so as not to alarm the targeted victims. If you let this infection in, your security software should detect and remove it instantly, but if such software does not exist on your operating system, you are in trouble. As long as this malware can stay hidden, it can successfully encrypt all of your personal files, and only after that would it reveal itself. The infection does not need to stay hidden forever because the point is to convince you that only cybercriminals can assist you with the recovery of files. That is not true. The infection is part of the STOP Ransomware family, and a tool called ‘STOP Decryptor’ was developed. It is free, but it does not guarantee full decryption. Hopefully, it works for you, but in any case, you must delete Rezm Ransomware in the end.
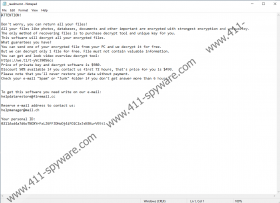
Rezm Ransomware has many clones, including Topi Ransomware, MOOL Ransomware, BBOO Ransomware, Reha Ransomware, and Nbes Ransomware. When these infections slither in and encrypt files, they always add unique extensions to them. Rezm Ransomware, of course, adds “.rezm.” Next to the encrypted files, you are likely to find a file named “_readme.txt.” This file was dropped by the malicious ransomware, but it is just a text file, and so opening it will not do any harm. At first, the message inside the file explains what has happened: “All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.” Next, it suggests that victims need to obtain a decryption tool and a decryption key to get the files back. The ransom note reveals that the price for this is $490, if paid within three days, which is why the infection is classified as ransomware. It is clear what the attackers want from you, but it is not clear how you are supposed to pay the ransom.
This information is concealed purposefully, because the attackers want you to contact them by sending an email message to either helpdatarestore@firemail.cc or helpmanager@mail.ch. You should not do that. If you contact the attackers, they will terrorize you, and even if they convince you to pay the ransom – which is unlikely to be exchanged for a working decryptor – they could continue terrorizing and scamming you anyway. Since you are unlikely to get the decryptor, you should not send messages or pay the ransom. If you are ready to do whatever it takes to get your files back, at least try using the free decryptor first. Also, think about what files could have been backed up in the past. If you have copies stored outside the computer, you do not need to worry about decryption. Your main concern is the removal of Rezm Ransomware. Note that if you want to check your backups first, you have to do that on a malware-free device. It is important that you delete Rezm Ransomware before replacing any of your personal files as well.
We hope that you have a way to restore or replace your files that does not involve paying a ransom for a decryptor that you are unlikely to receive. Now, let’s focus on the removal of the infection. You might be able to remove Rezm Ransomware by following the manual removal steps below. If this is your choice, do NOT skip the last step. Scanning your system with a trusted malware scanner is crucial because you do not want to overlook any other threats or even the leftovers of Rezm Ransomware itself. Of course, if other threats exist and if you are also looking into securing your system, the manual removal option is not for you. What you should do instead is install an anti-malware program that can automatically erase existing threats, with all of their components, as well as strengthen your system’s protection. Also, remember to always backup personal files because having copies is the best insurance against damage, loss, and malware attacks.
How to delete Rezm Ransomware
- Delete recently downloaded suspicious files.
- Delete all copies of the _readme.txt file.
- Launch Run by tapping Win+R keys and enter regedit into the dialog box.
- In Registry Editor, go to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
- Delete the value called SysHelper (its value data should point to %LOCALAPPDATA%\[random name]\[random name].exe/%USERPROFILE%\Local Settings\Application Data\[random name]\[random name].exe).
- Launch File Explorer by tapping Win+E keys.
- Enter %LOCALAPPDATA% or %USERPROFILE%\Local Settings\Application Data\ into the field at the top.
- Delete the [random name] folder that contains a malicious [random name].exe file.
- Enter %WINDIR%\System32\Tasks\ into the field at the top.
- Delete the task named Time Trigger Task.
- Exit Registry Editor, exit File Explorer, and Empty Recycle Bin.
- Install a legitimate, trusted malware scanner and perform a system scan to check for leftovers.
Rezm Ransomware Screenshots: