Righ Ransomware Removal Guide
It does not take much for an infection like Righ Ransomware to invade a vulnerable operating system. Those who face this malware usually do not have reliable protection set up, because of which, the threat steps inside and stays hidden for as long as that is needed. Of course, even if your system is completely unprotected, you could still manage to secure your operating system. However, most users are careless, and they also lack knowledge about how malware works. Do you know how ransomware spreads? According to our malware researchers, the infection is most likely to slither in using spam emails, malicious installers, or RDP vulnerabilities. You could open these security backdoors even if you had your system protected, but security software would delete Righ Ransomware before full execution. So, has this malware slithered in? Were your personal files encrypted? Do you need information about the removal? Keep reading.
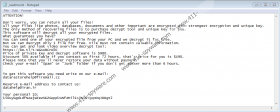
STOP Ransomware is the predecessor of Righ Ransomware, as well as Remk Ransomware, Lokd Ransomware, Rezm Ransomware, and a bunch of other well-known infections. They are completely identical, and it is even possible that they were created by the same attackers. Once inside the system, Righ Ransomware starts encrypting personal files immediately, after which, the “.righ” extension should be added to all of their names. To make it clear what is going on, the infection also drops its own file, which is named “_readme.txt.” It is originally dropped to %HOMEDRIVE%, but copies could exist elsewhere. This file serves two purposes. First, it explains what has happened: “All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.” Next, it informs that only the attackers can help recover files: “The only method of recovering files is to purchase decrypt tool and unique key for you.” The “price” for the tool is $980/$490 (depending on the time of the payment), and this is what we recognize as the ransom.
Although the ransom note presented by Righ Ransomware makes it clear what the attackers want, it is not possible to pay the ransom right away. First, you are supposed to email datarestorehelp@firemail.cc and/or datahelp@iran.ir. If you do this, you should receive additional instructions on how to pay the ransom in Bitcoin, a virtual currency that is often employed by cybercriminals, especially ransomware creators and operators. You might think that sending a message to the attackers is not a dangerous move. Well, if you use your own email account, they could use this bridge to expose you to all kinds of emails, and they are unlikely to stop even if you pay the ransom in full. Speaking of the ransom, we do NOT recommend paying it. Why? First of all, you will get nothing for it. Second, have you tried employing the Stop Decryptor? This is a free tool that was created by security experts, and while there are no guarantees that it would restore the files corrupted by Righ Ransomware, you certainly want to explore every avenue before you take huge risks.
If you have copies of personal files stored outside the infected computer, you also can replace the files corrupted by Righ Ransomware. Of course, this can be done only after the removal of the infection. The elimination of this malware can be both simple and complicated. That all depends on your own expertise and knowledge. If you can identify malware files, go ahead and follow the instructions below. If you cannot remove Righ Ransomware manually, perhaps you should install a tool that would handle the infection automatically? Our malware researchers always recommend implementing anti-malware software because besides providing users with full malware removal services, it also can protect Window systems. As you now know, unprotected systems are the first ones to be hit by ransomware, and other kinds of malware for that matter. So, secure your system, have the infection removed, restore files using a free decryptor or your own backup, and always remember to stay safe online.
How to delete Righ Ransomware
- If you can find the {unknown name}.exe file that launched the threat, Delete it.
- Tap Win+E keys simultaneously to launch File Explorer.
- Enter %LOCALAPPDATA% into the field at the top to access the directory.
- Delete the folder with a long random name that contains ransomware files.
- Enter %HOMEDRIVE% into the field at the top.
- Delete the ransom note file called _readme.txt.
- Delete the folder called SystemID with PersonalID.txt file inside.
- Empty Recycle Bin and then immediately install a legitimate malware scanner.
- Perform a complete system scan to check if there are any leftovers.
Righ Ransomware Screenshots: