ROGER Ransomware Removal Guide
ROGER Ransomware is a dangerous computer infection, and it will try to rip you off by holding your files hostage. No matter what this program is going to tell you, you need to ignore it and focus on the malware removal. Please note that removing ROGER Ransomware doesn’t mean all the things this program did to your system automatically disappear, too. You need either a public decryption tool or a file backup to recover the encrypted data. If you feel at a loss of what you’re supposed to do, please be sure to address a professional technician nearby.
This annoying infection comes from the Crysis/Dharma Ransomware family. It means that there are multiple programs based on the same code, and they are released regularly with certain modifications. So, as far as the behavioral patterns and the removal steps are concerned, ROGER Ransomware is really similar to Dever Ransomware, Devil Ransomware, and many other programs that are ready to turn your life into a nightmare. The sad part is that it is quite easy to avoid getting infected with ROGER Ransomware. But users are seldom aware of the ransomware distribution practices, and they fail to notice suspicious files or documents when they reach the target systems.
For example, the most common way for ROGER Ransomware and other similar infections to reach victim computers is through spam. Spam emails drop into our inboxes every single day. For the most part, they should be filtered into the Junk folder, but the more sophisticated ones often reach the main inbox, too. Those emails look like various reports, invoice orders, and messages from your partners. It is especially easy to fall into the trap if you receive those messages at work.
What if you deal with such files every single day? What if the spam email that carries the malicious attachment doesn’t look any different from the documents you process regularly? What if you open the received files automatically? Then, there is definitely a bigger chance to get infected with ROGER Ransomware, and you would have no one else but yourself to blame for it. Therefore, it is strongly recommended to scan the received files with a security tool of your choice before opening them. Even better: if you do not recognize the sender and the message that the file comes with sounds urgent, you can simply delete the email, no questions asked.
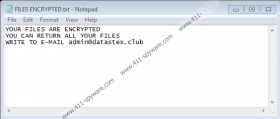
If you fail to avoid the infection and ROGER Ransomware reaches your computer, the infection will encrypt your files. All the affected files receive a new extension, but you really don’t need that additional line to find the encrypted files. The file icon will change and your system will no longer be able to read those files. What’s more, ROGER Ransomware will drop a ransom note in every affected folder, and it will also display a pop-up that tells you about the situation you’re in. Here’s an extract from the note:
YOUR FILES ARE ENCRYPTED
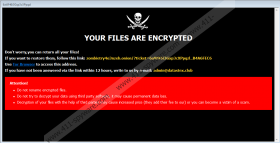
Don’t worry, you can return all your files!
If you want to restore them, follow this link: [link]
Use Tor Browser to access this address.
If you have not been answered via the link within 12 hours, write to us by e-mail: admin@datastext.club
ROGER Ransomware also says that you shouldn’t try to decrypt your data with third-party software because that could result in a data loss. It is not clear how true these claims are, but any security researcher would tell you that contacting these criminals is futile. You should remove ROGER Ransomware right now and then invest in a licensed security tool that would help you clean up your computer.
How to Delete ROGER Ransomware
- Remove the most recent files from Desktop.
- Open the Downloads folder and remove the most recent files.
- Access these directories with the Win+E command:
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%APPDATA%
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32 - Remove the Info.hta file and the random EXE file from the directories above.
- Press Win+R and enter regedit. Press OK.
- Open HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- On the right, right-click and remove the Info.hta and the random EXE file.
- Scan your computer with SpyHunter.
ROGER Ransomware Screenshots: