Rokku Ransomware Removal Guide
Rokku Ransomware is a computer infection which you will definitely not want to encounter because it is really harmful. If it ever slithers onto your computer, it will immediately encrypt all the files stored on it. Rokku Ransomware is not a unique ransomware infection. Specialists at 411-spyware.com have observed that it acts like Rush/Sanction Ransomware, Redshitline Ransomware, and Better_call_saul Ransomware. Like all these threats, Rokku Ransomware also seeks to extort money from users, which is why it acts the way it does. You should not give money for cyber criminals that hide behind this infection. The only thing that you really have to do if you have encountered this threat is to remove it from the system completely. We suspect that this will be a very difficult task for the majority of users because this infection does not have an uninstaller. Luckily, it does not block system utilities and Desktop like other well-known ransomware infections.
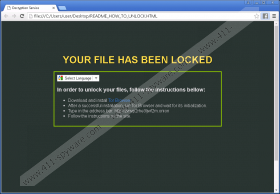
Researchers at 411-spyware.com have thoroughly tested Rokku Ransomware and found that this ransomware infection uses the RSA-3072 encryption algorithm in order to encrypt files stored on the computer. This means that it will not be easy to decrypt the files. In fact, this might not even be possible to do that if you decide not to pay a ransom. In such a case, the only way to gain access to files again is to restore them from a USB flash drive or some kind of external hard drive. Unfortunately, it seems that you will need to restore all the files that you kept on your system because Rokku Ransomware is going to encrypt all videos, music, pictures, and documents. To be more specific, it will encrypt files with the following extensions (of course, the list is not finite) and assign its extension .rokku to them: .max, .crw, .raf, .php5, .log, .fbk, .clx, .mp4, .raw, .dic, .eps, .kmz, .bak, .xns, .ob, .pub, .epsp, .prn, .dif, .doc, .docx, .fxg, .vib, .eml, .gifm .pict, .tif, .dib, and others. After doing that, it will also create two files readme.txt and readme.html with instructions and will put them on the screen. These files contain information about the decryption of files.
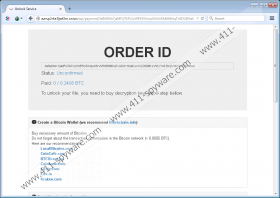
If you have already encountered Rokku Ransomware, there is no doubt that you know after opening and reading the information in readme.html or readme.txt file that you need a) to download the Tor Browser and b) type the provided URL in the address bar and c) follow the instructions on the website. This particular website will contain all the necessary information, but, most importantly, you will be instructed that you need to pay 0.2408 BTC for cyber criminals in order to download the decryptor. You could also be able to decrypt one file for free on the website. According to our researchers, the decryptor that will be available for download after you make a payment will unlock files. Of course, this will not cheer you up if you are not planning on paying a ransom.
Rokku Ransomware is very similar to other ransomware infections in a sense that it is usually spread as a MS Office Word document in Spam emails. Have you downloaded some kind of attachment recently? If so, it is not surprising at all that you have this ransomware infection on your system. We highly recommend that you ignore Spam emails and do not even open them for the sake of your system’s safety. You should, of course, also install a security tool on your computer and always keep it there if you do not want to cause harm to your system ever again.
The easiest and quickest way to get rid of Rokku Ransomware is to scan the system with an automatic malware remover. We suggest using SpyHunter for this matter because we know that this tool will help you to delete all the infections from your system. You can eliminate Rokku Ransomware manually as well – use instructions provided below this article; however, you will still have to take care of other infections existing on your computer. It is up to you whether to do that manually or automatically.
Delete Rokku Ransomware
- Find and delete the malicious MS Office Word or another suspicious file.
- Find and remove csrss.exe from %ALLUSERSPROFILE%\Windows or %ALLUSERSPROFILE%\Application Data\Windows, depending on the version of Windows OS installed.
- Remove Readme.txt and Readme.html files.
- Empty the recycle bin and restart the computer.
Rokku Ransomware Screenshots: