RSA Ransomware Removal Guide
RSA Ransomware is a threat you most likely want to avoid if you keep irreplaceable files on your computer and do not want to lose them. What this threat does is encrypt targeted data with a robust encryption algorithm. Next, it ought to show a ransom note, which should say you have to pay a ransom if you want your data to be decrypted. What should be clear is that no one can guarantee that the malware’s developers will hold on to their promise and that your money will not be lost in vain. Thus, we advise thinking carefully whether you wish to risk being scammed. Also, we recommend removing RSA Ransomware if you do not want to endanger new files you might yet create or receive. If you want to learn why deleting this threat might be a good idea, we recommend reading the rest of our article. As for learning how to get rid of it manually, you should check the instructions located below.
RSA Ransomware might sneak in if your computes has weaknesses like unsecured RDP (Remote Desktop Protocol) connections, or it could settle in after interacting with Spam emails or any unreliable data downloaded from the Internet. Therefore, we recommend strengthening your system if it has any weaknesses and avoiding interaction with files you are not entirely sure to be reliable. Also, if you do not want to take any chance, we recommend scanning downloaded or received data with a chosen antimalware tool. That way, you will know if a file is dangerous or not before opening it. Just make sure that the security tool you select is legitimate and that reputable developers created it. Also, it is vital that you download it from a legit source. Otherwise, you could end up installing a fake or rogue antivirus tool.
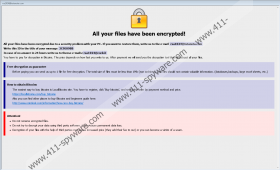
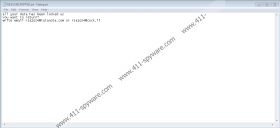
You may not notice that RSA Ransomware entered your system as it works silently in the background until targeted personal files like photos and documents are encrypted. Each file affected by this malware should receive a second extension made from a unique ID number, an email address, and the abbreviation (RSA) of a specific encryption algorithm, for example, .id-3C9E098B.[rsa1024@tutanota.com].RSA. Such files become unreadable, and the infected computer should become unable to open them. They can be restored, but only with unique decryption tools that only the malware’s developers might have. According to the threat’s ransom note that it leaves after encrypting files, the hackers behind RSA Ransomware want to receive a payment in Bitcoins and promise to deliver decryption tools afterward. As said earlier, there is not knowing whether they will provide such tools as promised or if they will still have them. Thus, we advise considering their demands carefully and not to pay if you decide it is too risky.
It is advisable to delete RSA Ransomware because the malware can auto start with your computer’s operating system, which means it might repeat the encryption process over and over again every time the device is restarted. Thus, if you do not want to endanger files that you might create yet, we recommend removing RSA Ransomware. To get rid of it manually, you could use the instructions located below. If you want an easier way, we suggest getting a reputable antimalware tool that could detect and erase such a threat.
Get rid of RSA Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Erase files called FILES ENCRYPTED.txt.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name, and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it, and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
RSA Ransomware Screenshots: