Rush Ransomware Removal Guide
If you cannot open any of your files, including, documents and pictures, there is a possibility that Rush Ransomware has sneaked onto your computer. This threat does not differ much from other ransomware infections because it also seeks to extort money from users. In order to make users pay money, this infection locks all the files and then asks users to pay a ransom. Luckily, it does not block .exe files and system utilities. In addition, it does not add any executable file to the system Startup like other similar infections. It means that it will be slightly easier to delete Rush Ransomware from the system. Unfortunately, this will still not help you to gain access to files. Do not worry; it does not mean that you cannot recover them.
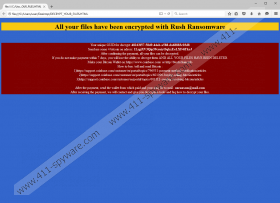
As Rush Ransomware seeks to extort money from users, it is not surprising that this infection will immediately encrypt all kinds of files the moment it sneaks onto the computer. Researchers working at 411-spyware.com have tested Rush Ransomware and found that it will encrypt files with the following extensions: .ppt, .pptx, .jpg, .png, .csv, .sql, .mdb, .php, .asp, .aspx, .html, .xml, .psd, .txt, and .pdf. After doing that, it will drop the DECRYPT_YOUR_FILES.html in all the major directories, including %ALLUSERSPROFILE%, %APPDATA%, %USERPROFILE%, and %WINDIR%. You will probably see it on the Desktop as well. If you open that file, you will immediately notice the message saying that “All your files have been encrypted with Rush Ransomware.” This file will also contain information on how to decrypt them. At the time of writing, Rush Ransomware is asking 4 Bitcoins (approximately 1600 dollars) for the decryption. The ransom has to be transferred to cyber criminals within 7 days. Evidently, cyber criminals behind Rush Ransomware seek to scare users into making a payment as soon as possible because it is written in the message that all files will be deleted if the user does not pay money within the stated time. You are the one who can decide what to do; however, if we were you, we would not send money to cyber criminals because it is also possible to recover files from a backup or external storage. Unfortunately, you cannot do that if you have never backed up your files.
Rush Ransomware is called like that because it adds the .rush extension to all the encrypted files. Specialists have also noticed that an identical ransomware infection with a different name (Sanction Ransomware) exists as well. In this case, it adds the .sanction extension; however, it is identical to Rush Ransomware in other respects. Like other ransomware infections, they usually sneak onto computers without permission. In case of Rush Ransomware, this infection is usually spread as a legitimate-looking MS Office Word file. It usually comes as an attachment in spam emails. As it does not look harmful at all, users open the email and download the attachment without any fear. This ransomware infection immediately sneaks onto the computer if a user does that. If you are sure that you have not opened any kind of email recently, it is possible that this threat has sneaked onto your PC together with other programs from third-party web pages. Rush Ransomware might have entered your system if it is not 100% clean as well. It is not so easy, but it is still possible to prevent ransomware infections from slithering onto computers. There is only one thing you have to do – to install a security tool on the system and keep it there all the time.
Even though Rush Ransomware was only detected on the 13th of February, 2016, it is already quite prevalent and the number of infected systems is growing considerably. As it is quite a widespread infection, it is very likely that many users will need to delete it from their systems. Unfortunately, the removal process is quite difficult because Rush Ransomware does not have an uninstaller, and it places its file in several main directories. We hope that instructions provided below this article will help you to deal with this ransomware infection manually. If not, you can download the SpyHunter scanner from this website (click on the Download button) and then scan the system. All the threats will disappear in the blink of an eye when you click the Fix Threats button after the system scan.
Remove Rush Ransomware
- Open the Windows Explorer (press Windows + E keys on your keyboard).
- Locate the DECRYPT_YOUR_FILES.html file in the following directories, delete it, and then empty the recycle bin:
- %ALLUSERSPROFILE%\Start Menu\Programs
- %APPDATA%\Microsoft\Windows\Start Menu\Programs
- %USERPROFILE%\Microsoft\Windows\Start Menu\Programs
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs
- %WINDIR%\System32\Tasks
- %WINDIR%\Tasks
Rush Ransomware Screenshots: