Sglh Ransomware Removal Guide
If you thought that ransomware is taking a break for Christmas, better think again. Sglh Ransomware is yet another addition to the STOP Ransomware family, and this program is here to target your money. The infection can encrypt your files and leave you scrambling to restore your data. You can remove Sglh Ransomware by following the manual removal instructions that we have provided below this entry. Also, there might be a way to restore your files, but it all depends on the encryption key that was used by the program. So, let’s dive deeper into this issue and see what it’s all about.
As mentioned, Sglh Ransomware comes from the STOP Ransomware family. Thus, we can see that this program is practically identical to Geno Ransomware, Foqe Ransomware, Vpsh Ransomware, Efji Ransomware, and many other programs we have discussed recently. It seems that all of them get released only after minimal tweaking, and they tend to be based on the same coding. What’s more, it means that this infection employs the same distribution methods, too.
Hence, to avoid Sglh Ransomware and other similar infections, you have to keep in mind how ransomware spreads around. The most common way for this type of programs to reach you is the spam email campaigns. They can be random, and they can also be targeted at a specific company or businesses. Whichever it might be, the bottom line is that you should avoid opening emails from unknown parties, especially if they come with outgoing links and attached files that supposedly require immediate attention.
When an email you haven’t been expecting demands that you check the attached file or click an outgoing link, it’s the first sign that it could either be a scam or a malware attack vector. Unfortunately, a lot of users do open those attached files because their curiosity gets the better of them. The moment they open those files, Sglh Ransomware infection is takes place as the download sequence is initiated, and malware reaches the target system. Once the infection is there, it scans the computer locating all the files it can encrypt, and the encryption takes place.
It doesn’t take long for your files to get encrypted. When the encryption is complete, you will see that the affected files get the .sglh extension, that works kind of like a stamp. It says which files were encrypted. Also, there is a ransom note in the C:\ directory under the _readme.txt filename. The ransom note is almost the same across all the other STOP Ransomware infections. Here’s what it has to say:
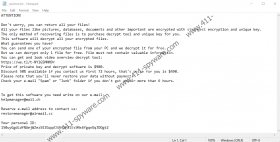
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
<…>
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Sounds like a good deal, but believe us when we say, it isn’t. Paying the ransom doesn’t guarantee you would get your files back. In fact, you might want to try the public decryption tool that has been developed for the STOP Ransomware infection. If Sglh Ransomware used an offline encryption key to lock up your files, you should be able to use the public decryption tool to restore your data.
Also, you should consider creating a file backup that is a definite go-to when a ransomware program strikes. You can always remove the infection and the encrypted files, and then transfer the healthy copies back into your computer that has had all the malicious programs removed.
How to Remove Sglh Ransomware
- Delete the latest files from your Desktop.
- Go to the Downloads folder.
- Remove the latest files from the folder and press Win+R.
- Type %TEMP% into the Open box. Press OK.
- Delete the latest files from the directory.
- Press Win+R and enter %LOCALAPPDATA%. Press OK.
- Remove the folder with a long random name from the directory.
- Use SpyHunter to scan your computer.
Sglh Ransomware Screenshots: