Shrug2 Ransomware Removal Guide
If you can see the “.SHRUG2” extension attached to your files, and you cannot open them normally, Shrug2 Ransomware must have invaded your Windows operating system. The threat must slither in without your notice or using a disguise, and so you might be unable to pinpoint the moment it happened. Maybe you do remember opening a suspicious spam email attachment or downloading a new program? Unfortunately, if you do not understand that malware got in, you are unlikely to remove it right away, and if you wait, the infection silently encrypts your personal files. This is how Shrug Ransomware, CryptConsole v3 Ransomware, Cryptolite Ransomware, and most other malicious threats work as well. If you browse our website, you will see that ransomware is dominating the world of malware right now. Unfortunately, it is unlikely that we will start seeing less of them any time soon because they can be very lucrative. Hopefully, you will not be tricked into paying any money, and, instead, you will focus on deleting Shrug2 Ransomware.
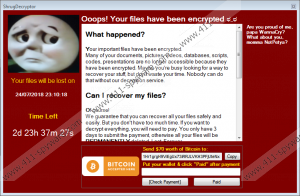
Once in, Shrug2 Ransomware uses an encryption key to take over your personal files. Once the data of the files is encrypted, they cannot be read. Files with .txt, .docx, .xls, .doc, .xlsx, .ppt, .pptx, .odt, .jpg, and .png extensions are among many other files that are corrupted by the infection. According to our tests, the infection should encrypt files only in the main Windows drive containing system files. Usually, it is the C:/ drive. The infection does not create ransom note files, but it launches a window called “Shrug Decryptor.” It can be launched using the @ShrugDecryptor@.lnk file created by the ransomware on the Desktop. This is where the demands are displayed, along with a timer that gives 3 days. The message instructs to make a payment for a decryption service that, allegedly, can guarantee full recovery of files. The ransom note also instructs to delete antivirus software if it exists, but that is unlikely to be a problem for you. Speaking of antivirus software, you must realize by now just how important it is to install reliable and efficient security software that would keep malware away or remove it when it attacks.
The form at the bottom of the window launched by Shrug2 Ransomware informs that you must “send $70 worth of Bitcoin” to a specific Bitcoin wallet (1Hr1grgH9ViEgUx73iRRJLVKH3PFjUteNx). Allegedly, once you pay the ransom, enter your own wallet address into the field and click the “Paid” button, your files are bound to be decrypted. Would that happen? That is very unlikely. Our research team has plenty of experience with file encryptors, and so we know that the promises made by cyber criminals are almost never kept. Of course, 70 Dollars is a relatively small sum, and you might be willing to take the risk. Just remember that if you pay the ransom, you will not be able to get your money back even if files are not decrypted. What can you do to protect your personal files in the future? Although it is extremely important that you protect your operating system against malware, it is also a good idea to back up files online or using removable drives. If files are backed up, you can access them even if malicious software corrupts or destroys them. By the way, Shrug2 Ransomware can delete the corrupted files once the timer on the ransom note window runs out.
The shortcut file, the HKCU/ShrugTwo registry entry, and the launcher of the ransomware are the main components you need to think about if you are choosing to remove Shrug2 Ransomware manually. We cannot say that you will not be able to erase the threat manually, but the process is certainly complicated if you lack experience. The bottom line is that the ransomware is not the only thing you need to think about. It is probably more important to think about virtual security in the future. You will not need to worry about this if you install trustworthy anti-malware software that will, at the same time, automatically delete Shrug2 Ransomware as well. You’ve got your recommendation and your information. Hopefully, you are ready to take the next step. If you still have questions, use the comments section.
How to delete Shrug2 Ransomware
- Find the .exe file that launched the ransomware, right-click it, and select Delete. It could be located in %USERPROFILE%\Downloads, %USERPROFILE%\Desktop, and %TEMP% directories.
- Move to the Desktop, then right-click the file named @ShrugDecryptor@.lnk, and select Delete.
- Launch RUN (tap Win+R keys) and enter regrdit.exe to access Registry Editor.
- Move to HKEY_CURRENT_USER, then right-click the key named ShrugTwo, and choose Delete.
- Empty Recycle Bin and immediately use a legitimate malware scanner to run a full system scan.
Shrug2 Ransomware Screenshots: