TurkStatik Ransomware Removal Guide
TurkStatik Ransomware is a computer infection that is intended for the Turkish-speaking users. Just like most of the ransomware programs on the market, this one also encrypts your files and holds them hostage. The idea behind it is that users are forced to pay the ransom for the decryption tool. However, you should never pay a single cent to these criminals. Remove TurkStatik Ransomware today, and then restore your files using a public decryption tool. Luckily, there is a public decryption key available for this infection. But we might not be that lucky the next time, so please protect your system from similar threats.
How is it possible to protect yourself from a ransomware infection? One, you should learn how these programs spread around. And two, you should make copies of your files in the case a ransomware program still manages to enter your PC.
For instance, we are sure that TurkStatik Ransomware entered the target system via spam email attachments. That is the classic example of a ransomware distribution network. Although the infection success rate via spam emails is relatively low, the sheer abundance of spam emails still makes it an attractive distribution method for cyber criminals. It is cheap, and it is easy to spread.
In some cases, spam emails that bring dangerous attachments may look like official notifications from reliable sources. For example, they might remind you of online shopping invoices or it could look like a personal notification from your business partner. However, you should make it a habit to scan the attached files before opening them. All the more so if you haven’t expected a particular email, and now it comes with an urgent message to check the attached documents. That’s automatically suspicious!
Also, you should back up your files regularly. The latest operating system versions maintain that backing your files up is the best remedy against ransomware because you won’t have to worry about retrieving your data in the case there is no public decryption tool. Of course, that is not the case with TurkStatik Ransomware, but it’s always better to be safe than sorry.
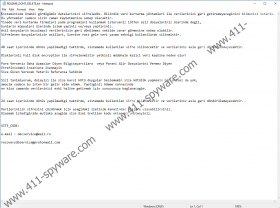
When TurkStatik Ransomware enters the target system, this infection coded in the .NET programming language will encrypt all logical drives, including networks, USB, and partitions. The encrypted files will get the “.ciphered” extension added to their filenames. Although you don’t really need that extension to figure out that your files have been tampered with. Also, the program drops a ransom note in every single location where the encrypted files are. Needless to say, the ransom note is in Turkish, but we get the gist of it just by looking at the translation:
We have encrypted your important data on your system. We would like you to know that you cannot restore your data with familiar data recovery methods.
These methods will only waste your time.
<…>
If no return is made within 48 hours, the password used in the system will be delete and your data will never be restored.
To put it simply, TurkStatik Ransomware says that you have to contact these criminals within 48 hours, and if fail to do so, you will never get your files back. That is obviously not true. You can restore your files with a public decryption tool, so you should start with removing TurkStatik Ransomware without any further ado.
If you happen to have a file backup, you can delete the encrypted files and transfer the healthy copies into your computer once TurkStatik Ransomware is removed. If you don’t have a file backup, please make one the moment you restore your data.
How to Delete TurkStatik Ransomware
- Remove the ransom note from the affected directories.
- Delete the newest files from Desktop.
- Go to the Downloads folder and delete the most recent files.
- Press Win+R and enter %TEMP%. Press OK.
- Remove the most recent files from the directory.
- Run a full system scan with SpyHunter.
TurkStatik Ransomware Screenshots:
TurkStatik Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | 6b583d07cfccac5ca23ccd73db14cb0cce09d14f179d63e65155fc451dace863 | 23552 bytes | MD5: 2AC37E496D2CA94547AE59691D8DFD61 |

