Zepto Ransomware Removal Guide
If your computer becomes infected with Zepto Ransomware, then all of the files on it will be encrypted, and you will have to choose between removing this malicious program and paying the hefty ransom for the decryptor needed to decrypt them. The people behind this malicious program want you to pay 1.5 BTC (an approximate 909.66 USD) which is a lot of money, so you should evaluate your files and also take into account the possibility of not receiving the decryption tool.
Zepto Ransomware is actually a variant of Locky Ransomware. These two programs are nearly identical, and it is impossible to talk about this new infection without having to mention Locky Ransomware. The only difference between these two infections is that Zepto Ransomware not only adds a different file extension (.zepto) when encrypting the files but also changes the names of the encrypted files. For example, it will change the file name to YYFYSDXF-ENBJ-GSDF-0C80-4C970BE3F009.zepto. Now, the first three sequences are the encryption ID number (YYFYSDXF-ENBJ-GSDF), and the last two sequences (0C80-4C970BE3F009) are generated randomly.
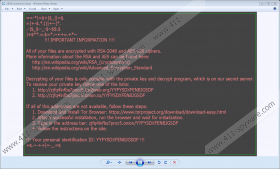
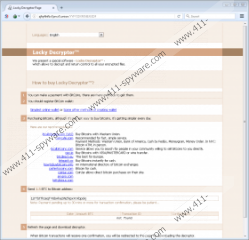
Another similarity or oddity, rather, is that Zepto Ransomware uses the same site as Locky Ransomware that you can only access using the TOR web browser. The developers did not bother to create a website dedicated to this new ransomware and the decryption tool named Locky Decryptor is supposed to work on the encryption keys of both of these applications. As mentioned, the decryptor costs 1.5 BTC but be warned that the decryptor might not work.
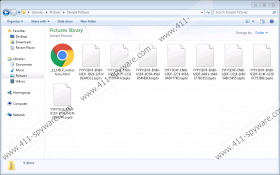
Evidently, this ransomware uses the AES-128 encryption algorithm to encrypt the files and the RSA-2048 to encrypt the decryption key, and the resulting decryption key is sent to the remote Command and Control Server that is managed by this ransomware’s developers. Once the encryption is complete, this malicious program will create two harmless files. One is called _HELP_instructions.bmp and is set as the desktop wallpaper and _[random number]_HELP_instructions.html that is dropped in each file where a file has been encrypted. Note that the random number is different in each folder. Once everything is in place, it is too late to do anything about this infection because, unless you have an antimalware program on your computer, the encryption cannot be stopped. Now let us discuss Zepto Ransomware dissemination methods.
Ransomware can be distributed using various techniques. Some are distributed with the help of exploit kits that are injected into hacked websites while those developers that are unable to set up a sophisticated exploit kit tend to use email spam. Hence, we have found that this program is disseminated using email spam. The emails feature zipped file attachments that are disguised as invoices and bank reports. Previously, this ransomware was distributed using zipped JS (JavaScript) files. However, now it is being sent as zipped WSF files (Windows Script Files) that are executed by Windows Script Host. Our research shows that the WSF files contain can contain both JScript and VBScript code. As a result, Zepto Ransomware is set to infect your computer secretly.
In conclusion, Zepto Ransomware is a highly malicious application whose purpose is to encrypt your personal files and “offer” you to buy the decryption key. This extortion scheme is set to make its developers a healthy profit unless you refuse to pay the ransom. In any case, we do not recommend trusting them to give you the decryptor once you have paid. Therefore, we encourage you to act decisively and delete this infection using an antimalware program. We have included a manual removal guide below if you want to get rid of it without additional software. However, you will have to identify its randomly named executable on your own.
Removal Guide
- Find and delete the main executable.
- Remove _HELP_instructions.bmp from the desktop
- Delete all copies of _{count digit}_HELP_instructions.html
- Empty the Recycle Bin.
Zepto Ransomware Screenshots: