ZeroLocker Removal Guide
ZeroLocker is a major threat to the health of your personal files. If you are a lucky computer owner whose operating system has not been affected by this threat yet, we suggest you immediately back up most sensitive and valuable files, and install authentic malware removal software to defend the system against malware attacks. Unfortunately, if you are reading the report, it is possible that you already need to delete ZeroLocker. This threat is identified as a ransomware because schemers have developed it to corrupt the operating system in the hopes of coercing you into paying a ransom fee. Here are a few excerpts from the ransom request.
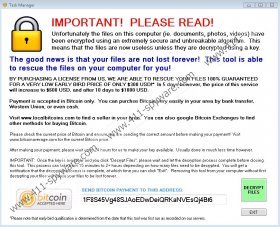
Unfortunately the files on this computer (ie. documents, photos, videos) have been encrypted using an extremely secure and unbreakable algorithm. This means that the files are now useless unless they are decrypted using a key.
By purchasing a license from us, we are able to rescue your files 100% guaranteed for a very low early bird price of only $300 USD! In 5 days however, the price of this service will increase to $600 USD, and after 10 days to $1000 USD.
Unfortunately, the developers of ZeroLocker are not joking when they are telling you that the files on the system are encrypted using an ‘unbreakable algorithm’. In fact, the encryption is so complicated that malware researchers have doubts whether the corrupted files will be salvageable, which means that your ransom payments may be completely ineffective. The same risks apply to the victims of Cryptowall, CryptoLocker, and similar infections which you must delete.
The devious infection runs a command cipher.exe, and it is responsible for creating multiple temp files within the folder EFSTMPWP. The infection overwrites files, which means that you will not be able to decrypt them yourself. If having the encrypted files removed does not interest you, and you are thinking about paying the ransom, you need to be very careful with the files you interact. You should not delete ZeroRescue.exe, address.dat and log.dat found within the folder under C:\ZeroLocker, or remove registry entries related to the infection.
It has been revealed that ZeroLocker can encrypt the registry file NTUSER.DAT which contains user configurations in Windows. When this file is encrypted, you may discover that shortcuts on the Taskbar are encrypted as well. Luckily, this does not necessarily mean that you will not be able to access your browsers, connect to the Internet and, most importantly, install automatic ZeroLocker removal software. Note that if you choose to delete the malicious encryption Trojan now, you will lose the questionable opportunity to restore the encrypted files.
The manual ZeroLocker removal is extremely complicated, which is why we suggest assigning reliable, automatic malware removal software to delete it from the PC. You should keep this software active at all times to ensure that the operating system is safeguarded against various malware attacks. It has been discovered that ZeroLocker is distributed with the help of fictitious Java installers, and this is something you can avoid easily with the right malware removers in action. Note that you need to install this software to delete the Trojan even if your files have been decrypted after paying the demanded fees. Has this happened? Post a comment below to share your experience.
ZeroLocker Screenshots: