Zobm Ransomware Removal Guide
Zobm Ransomware is another version of Stop Ransomware. Like most of such threats, it asks users to pay a considerable amount of money in exchange for getting decryption tools that are supposed to restore the malware’s locked data. If you do not think it to be wise to trust hackers and do not want to put your money at risk, we recommend ignoring the threat’s warning. Users who have backup copies son cloud storage, removable media devices, or anywhere else safe, should be able to replace encrypted files with them. However, we do not recommend uploading backup copies on an infected machine. It would be safer to remove Zobm Ransomware first. To learn how to do so as well as more details about this malicious program, we invite you to read our full report and check the instructions located below it.
Malicious applications like Zobm Ransomware are often distributed via unreliable messages (e.g., Spam emails) and websites (e.g., torrent or similar file-sharing sites). Also, they might be able to enter a system by exploiting their weaknesses. Usually, such threats can use unsecured Remote Desktop Protocol (RDP) connections, so it is advisable to make sure such connections are secure. Also, if you want to protect your device from similar malware, we recommend scanning files received from senders you do not know or obtained from untrustworthy websites with a reliable antimalware tool. If you open the file first, it might be too late to do anything to protect your computer, so it would be wiser to invest a bit of your time and scan questionable files first.
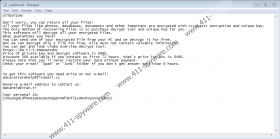
Our researchers say that Zobm Ransomware should settle in like most of the other threats from the Stop Ransomware family. Many of them create copies of their launchers in a folder with a long and random name that should appear in %LOCALAPPDATA%. Afterward, the malware should start encrypting files, and during this process, each locked file ought to receive a second extension called .zobm, for example, text.docx.zobm. At the end of the encryption process, the malware should drop a couple of documents called PersonalID.txt and _readme.txt. The first one might carry a unique ID number that the threat might give to an infected device. As for the second document, it should contain the malware’s ransom note. Zobm Ransomware’s ransom note should ask you to pay $490 within 72 hours or $980 if you do not make the payment on time. The sum is considerable, as there are hackers who ask for less than $100.
It is only up to you to decide if your files are worth taking any chances. As you see, even if hackers claim they promise you will receive the decryption tools they claim to have, there are no reassurances that they will do so. Cybercriminals could take the received ransom without sending the promised tools as well as ask for more money. If you decide you do not want you to put your savings at risk, we advise against following the instructions displayed on the threat’s ransom note.
As said in the beginning, it might be safer to remove Zobm Ransomware if you plan on transferring backup copies. Also, it might be safer for your future data as well since it was noticed the malicious program might auto-start whenever you restart or turn on your device. To eliminate Zobm Ransomware manually, you could use the deletion instructions located below. For users who find the task too challenging, we recommend employing a trustworthy antimalware tool.
Get rid of Zobm Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Search for files named _readme.txt and PersonalID.txt, right-click them, and select Delete.
- Check this location: %LOCALAPPDATA%
- See if you can find the malware’s folder with a random name, e.g., 0215171b-ba55-7xal-a49s-c2fk4162159c, right-click it and choose Delete.
- Close File Explorer.
- Empty Recycle Bin.
- Restart the computer.
Zobm Ransomware Screenshots: