Zorgo Ransomware Removal Guide
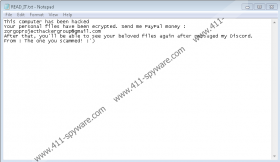
Zorgo Ransomware encrypts files and adds an extension called .zorgo at the end of all affected files. Also, victims of the threat should receive a ransom note saying that they must transfer money to the hackers’ PayPal account if they want to decrypt their data. Of course, we recommend against it because you cannot know for sure if hackers will hold on to their end of the bargain. If they do not, you could lose not just your photos or other files that got encrypted but also your money. To learn more about this malicious application before you decide what to do, we invite you to read our full report. For users who decide they want to erase Zorgo Ransomware instead of dealing with hackers, we can offer our deletion instructions located at the end of this article.
Zorgo Ransomware could be spread through Spam emails as many ransomware applications are distributed this way. Our specialists believe that users who receive the malware could get a message saying that they need to open an attached PDF file. That is because our encountered sample of the threat had a PDF file’s icon. Consequently, users who receive or download the malicious application’s installer might think that it is harmless. To avoid making a mistake of opening a harmful file unknowingly we advise scanning files obtained from the Internet, especially, if they come from unknown senders or questionable websites, with a reliable antimalware tool first to find out if they are safe to interact with.
After it is launched, Zorgo Ransomware should create a couple of files in the C:\{username}\Rand123 location. Our specialists say that one of the files ought to be a malicious executable file, while the other one should be a JPEG picture. It seems that the malware is supposed to use the mentioned picture to change victims’ wallpapers, but the sample we found failed to do so. In any case, before changing the Desktop image, the malicious application should encrypt all data that is not associated with the operating system or other software. It means, the threat might encrypt various types of documents, pictures, and so on. Once such files are locked, Zorgo Ransomware should create a document named READ_IT.txt that ought to contain the malware’s ransom note. According to the note, users can get their files decrypted, but they must pay ransom and get in touch with hackers via Discord.
Once again, we do not recommend paying ransom because you cannot be certain that hackers will be able or willing to decrypt your files even if you do as they ask. Also, users should know that Zorgo Ransomware was based on Hidden-Tear Ransomware. At the time when threats from this family were popular cybersecurity experts came up with a decryption tool that allowed to decrypt at least some files. If you have no other way to restore your files, you could try to look for the Hidden-Tear decryptor; just make sure that it comes from cybersecurity experts and not some shady website.
Lastly, we advise deleting Zorgo Ransomware if you do not want to pay ransom or leave a malicious application on your system. There is a way to get rid of it manually and if you look at the instructions located below, you can learn about it. As for users who fear they might be unable to deal with such a threat manually, we recommend employing a reliable antimalware tool. In such a case, you should perform a full system scan and then click the removal button presented by your chosen antimalware tool to eliminate Zorgo Ransomware for good.
Get rid of Zorgo Ransomware
- Launch Task Manager and go to Processes.
- Locate a process belonging to the malware.
- Select it and press End Task.
- Exit Task Manager.
- Tap Win+E.
- Check these folders:
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads
%TEMP% - Locate the threat’s installer, which might look like a PDF file, right-click the malicious file, and press Delete.
- Navigate to: C:\{username}\Rand123
- Locate the following files:
local.exe
ransom.jpg - Right-click the mentioned files separately and press Delete.
- Check your Desktop and find a document called READ_IT.txt, right-click it, and select Delete.
- Exit File Explorer.
- Empty Recycle Bin.
- Restart your computer.
Zorgo Ransomware Screenshots: