Reveton hits android users
It is no surprise that the android platform gets hit by malware for the second time, as it is the leading operating system on mobile devices. This time itis Android Reveton; the first infection to hit the mobile systems back in June of 2013 is known as Android FakeAV. This particular new type of malware is known in the industry as Android.Trojan.Koler.A. The name Android Reveton was adopted because of the close resemblance to the traits of Reveton malware that has been active on Windows operating systems for some time now.
Furthermore, it is believed that it was developed by the same gang of cyber-criminals that developed and distributed the original Reveton ransomware. Fortunately, it is relatively simple to remove Android Reveton off your device. There are a lot of speculations among the security community if this particular version was crafted as something of a trial version by the cyber-criminals. But it is obvious that targeting mobile devices had to be the next step of malware creators as its popularity grows so rapidly.
On one hand, there are a lot of similarities between the Android and Windows versions of Reveton. Both infections will lock up the interface of the device making it almost impossible to use, also both of them will ask for a ransom that's around the same price range of $300, which will be asked to pay via Ukash or MoneyPak. Furthermore, both will display warnings from law enforcement agencies based on the geography of IP address (a user in the US will get an FBI warning and the user in the UK will get a Metropolitan Police Department message). There is no doubt that both the Android Reveton and the PC one will make a lot of trouble on your devices.
On the other hand there are a few differences that separate these infections. One of the fortunate differences is that Android Reveton is easier to remove compared to its Windows counterpart. Arguably the main difference is the way that Reveton infection is spread around. A PC based infection most of the time does not require any authorization from the user. It infects the system silently and stealthily. This is not the case with the Android Reveton. The android user actually has to have sideloading enabled in their settings and they actually have to tap on the install button, thus allowing the infection to get installed on the device. The other noticeable difference between these two is the textual threat that is displayed on the device; in case of Android Reveton the user will see:
“Attention! Your phone has been blocked up for safety reasons listed below. All the actions performed on this phone are fixed. All your files are encrypted. CONDUCTED AUDIO AND VIDEO”.
The statement that the files on the device are encrypted is the main difference within the warning messages. It does not exist in case of PC infections. But the truth is that the statement about encryption is a total hoax, as no files on the device are actually encrypted, it is just a scare technique so ultimately the ransom would be paid. However, this could indicate something that the malware creators are focusing on, it might be that at the moment it is just a scare tactic, but eventually this is an ultimate goal – a CryptoLocker type of infection targeted towards the android users.
Another contrasting feature is that the users are actually able to get on to the interface by tapping the home button on their mobile device, although just for a few second. This might also highlight the idea that the infection may have been more of an experiment than an actual attempt for profit. The other difference is that once the infection is on the mobile device the cyber-criminals have your IMEI on file instantly. This means the the cyber-criminals have the ability to track your device at almost all times if needed. It is not clear whether this could be used in a broader sense in stealing personal information that is stored on users personal device. Yet Android Reveton seems more like a tryout version than the real thing, but you should still be cautions at all time as it is harmful for your device! Thus all users should be on alert for other infections that might be popping up in a near future.
It has been stated that Android Reveton spreads mostly and almost exclusively through browsing certain porn websites. Porn users have always been a major target of cyber-criminals and android users are no exception. As user browses a porn website, a fake video player downloads in order to let the user access premium slots on the website. By installing the player user gets infected. This particular application is found to be called and listed in the App sections as BaDoink.
Well the obvious piece of advice is: do not surf porn websites on your android device… Otherwise taking security measures in order to save time of having to remove Android Reveton is highly advised. Try and avoid downloading any apps from a third-party websites, these might be highly contagious. Safe browsing habits should be at the top of your list. Remember that any type of infection is harmful to any system whether it is an Android one or a Windows one. Remove Anroid Reveton ASAP!
Making the most of the security settings on your android device is required if you want to avoid Android Reveton.
- Keep your Wi-Fi, Bluetooth and Network data off as a default setting. Also make sure that Portable Hotspots and Tethering are switched off as a default a well. This will prevent any unwanted connections that might be malicious.
- Disable sideloading. This can be done by entering the settings menu and unchecking Unknown sources box. This will prevent the installation of apps from third-party vendors that most of the time could be quite suspicious.
- Check the Verify apps box. This means that before each installation of any kind of app you will be asked for permission first.
- Also check the Auto update security box in the security menu; this is important as you will be able to activate important security updates as soon as they are available.
Android Reveton is probably one of the many infections that will follow. Infecting Android devices had to start at some point, as these kinds of devices are becoming more and more popular in replacing the traditional systems concerning such simple everyday tasks as emailing, internet banking, internet shopping etc. Thus this means there is a lot of data that is at risk on the device. But the security professionals are not naive and professional Anti-Spyware tools for mobile devices are being produced even as we speak.
Remove Android Reveton:
Removing the infection is relatively simple, because just like in Windows, every Android device offers a safe mode option. And once the safe mode is loaded no third-party apps will load on your device so you will be able to remove the infection without a lot of trouble.
- Reboot your device into safe mode in order to remove Android Reveton. The way a device reboots into safe mode is different for different devices.
For Samsung Galaxy devices the way would be powering off your device and as soon as Samsung logo displays, you should start tapping on the Volume Down button, until the lock screen appears
For most of the HTC devices the way to reboot into safe mode is simply by holding the Power button on the device, tapping and holding the Power off option, then a pop-up will appear which will allow a safe mode reboot.
Most of others android devices will use either of these two methods in order to reboot the device into safe mode.Screens:
- Once in safe mode, get into the Settings menu and now go to the Application Manager subcategory. You will see the list of all the apps installed on your device. Select the malware, which in this case will go by the name BaDoink, tap on the app and remove it.
Screens: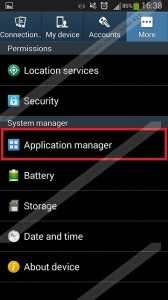
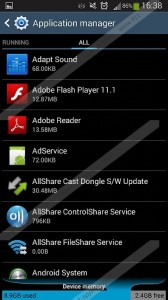
- Reboot your device back into normal mode, now your system is clean.

